24/7/365 Surveillance: Unceasing Protection
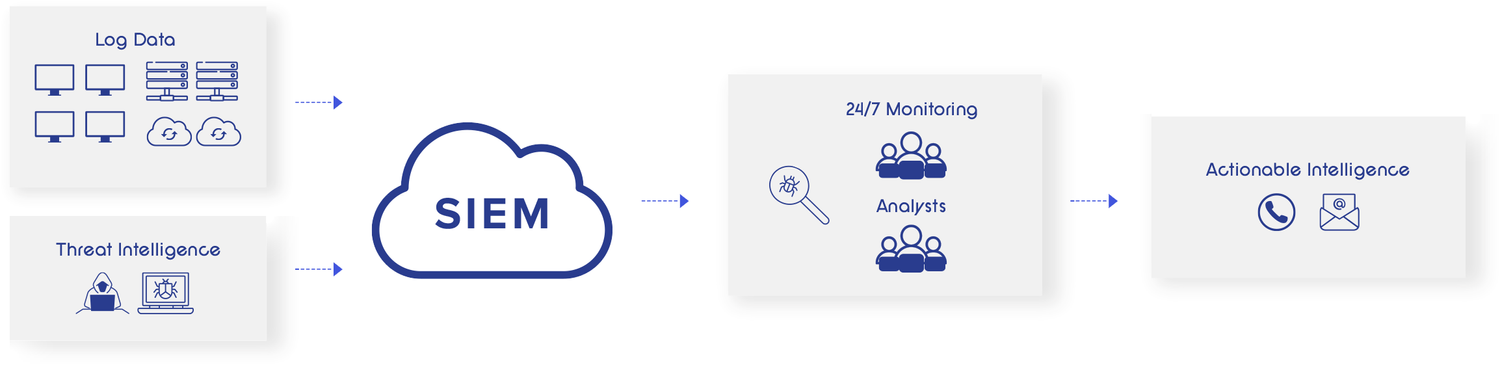
Zecureright Guard stands as the stalwart guardian for your organization, offering unwavering defense in an ever-evolving cyber threat landscape. Employing a proactive, prevention-first approach, Guard detects and alerts you to cybersecurity threats before they can inflict any harm, furnishing actionable intelligence to expedite the remediation process.This custom-built technological solution harnesses the might of big data, threat intelligence feeds, and the astute analysis of the Zecureright cyberthreat team. Guard operates around the clock, every day of the year, ensuring steadfast cybersecurity detection, timely notification, and effective remediation at any hour.
In the Realm of Cybersecurity, Early Detection is Paramount
Zecureright Guard seamlessly integrates across various devices, endpoints, applications, cloud platforms, and networks, channeling data into a centralized monitoring system. This system, fortified with big data and machine learning prowess, processes trillions of data logs in real-time, day and night. These logs are meticulously cross-referenced with advanced threat intelligence data, creating a comprehensive view of cybersecurity risks, the likelihood of an attack, and its potential severity. Should a malicious actor breach your security perimeter, the Zecureright expert security team swiftly assesses the threat, discerns false positives, and communicates with your organization accordingly.
 Raising Your Defenses
Raising Your Defenses
Equipping your organization with 24/7/365 cybersecurity protection is now more accessible than ever, thanks to our dedicated onboarding team. In just 6 weeks, Zecureright Guard’s experts collaborate with your team to establish data connections, configure security systems, and implement essential processes.
Preserving Your Digital Assets: A Wise ChoiceCyber threats never take a break. That’s precisely why Zecureright’s Guard solution is the right fit for all Australian enterprises. If your organization relates to any of the following scenarios, Guard is your answer.
- Cost-Effective Shielding
- Reduced Reliance on Internal Teams
- Board-Level Engagement
- Enhanced Watchfulness
When your IT and cybersecurity budgets are stretched thin, creating potential cybersecurity vulnerabilities, Guard steps in to provide preventative protection at a cost-effective price point.
For organizations grappling with the challenge of retaining IT and cybersecurity talent, Guard offers expert security guidance, analysis, and remediation from our Australia-based team.
As cybersecurity ascends to the Board Level mandate, Guard delivers monthly reports and Analyst Briefing meetings to keep the Board well-informed and engaged.
If your organization has recently faced a cybersecurity breach and now seeks heightened vigilance, Guard extends its protective shield to prevent and remediate all future cyber threats and attacks.
Discovering Critical Vulnerabilities that Truly Matter
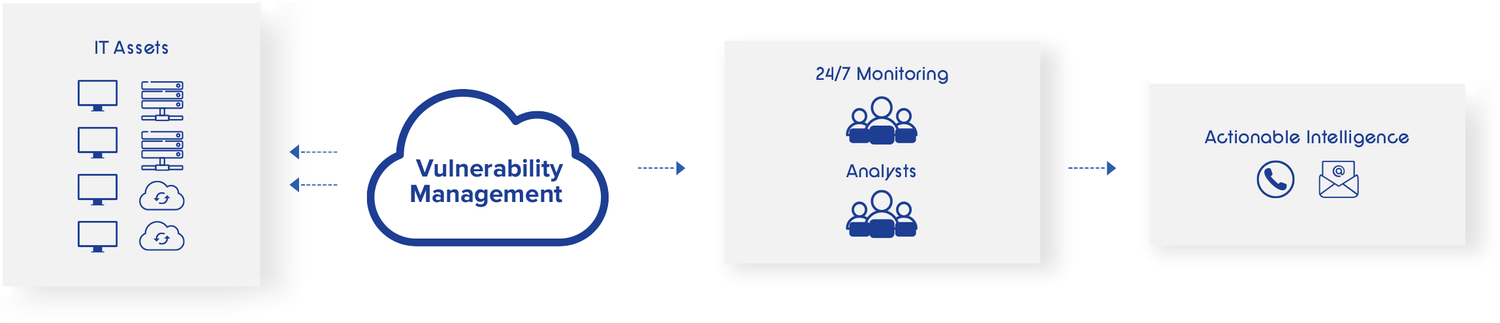
ZecureRight Detect empowers organizations to maximize their vulnerability management investments. Covering scaled cloud deployments, externally facing assets, and internal infrastructure, ZecureRight Detect combines our top-notch cybersecurity expertise to create a comprehensive vulnerability management program that provides profound insights into the cyber exposure of your assets.
ZecureRight Detect equips your organization to prioritize and defend against vulnerabilities, exploits, misconfigurations, and emerging cybersecurity threats that a standalone security technology cannot address.
Enabling Your IT Team to Achieve More with LessVulnerability Management tools, in isolation, often fall short in maintaining organizational security. They struggle to keep pace with the ever-evolving cybersecurity threats and the surging number of vulnerabilities across every layer of the IT environment. Additionally, overburdened IT and security teams find it challenging to address all vulnerabilities categorized as ‘high’ or ‘critical’ by the Common Vulnerability Scoring System (CVSS). ZecureRight Detect empowers your team to concentrate on what truly matters with a risk-based vulnerability management program, backed by a 24/7/365 approach managed by the cybersecurity experts within the ZecureRight team. ZecureRight Detect in Action: Streamlining Cybersecurity Vulnerability Management Across Your Organization
The Four Pillars of Vulnerability Management by ZecureRight Detect- Discovery and Scanning:
- Prioritization and Customization:
- Continuous Monitoring and Response:
- Real-time Assessment and Reporting:
ZecureRight collaborates with your team to locate and scan a wide array of accessible systems throughout your environment, necessitating vulnerability management. We cover laptops, desktops, servers, web applications, firewalls, cloud networks, switches, backup systems, infrastructure, printers, BYOD, custom libraries, and Java runtime environments, enrolling them into our platform. We identify open ports, outdated patches, and unprotected services against known vulnerabilities and current exploits. Customized reports, metrics, and dashboards are created to suit your organization’s specific needs.
The ZecureRight Detect team partners with your business to prioritize known vulnerabilities according to your organizational key priorities and risk management strategy. Recognizing that every organization is unique, common vulnerability frameworks (e.g., CVSS) often generate irrelevant alerts and unwarranted work for your overworked team. This evaluation process results in a low-noise, minimal-effort alert and remediation system that empowers your team to safeguard the most critical assets in an organized and efficient manner.
ZecureRight Detect offers 24/7/365 vulnerability management across your environment, proactively protecting and advising on nearby or impending cyber threats. Depending on the vulnerability, the ZecureRight Detect team collaborates with you on remediation, mitigation, or advised acceptance. The cybersecurity experts within ZecureRight work with your security team and system owners to determine and guide the appropriate remediation approach.
Enhancing the speed and accuracy of your vulnerability detection is pivotal to a robust risk management strategy. ZecureRight Detect consistently evaluates the effectiveness of your organization’s vulnerability management program and visualizes it through a tailored central dashboard suitable for Executive or Board Level reporting. With our active vulnerability notification and ticketing system for critical vulnerabilities, reporting is prioritized based on urgency, trends, and mitigation efforts
ZecureRight Protect: Elevating Your Organization’s Security
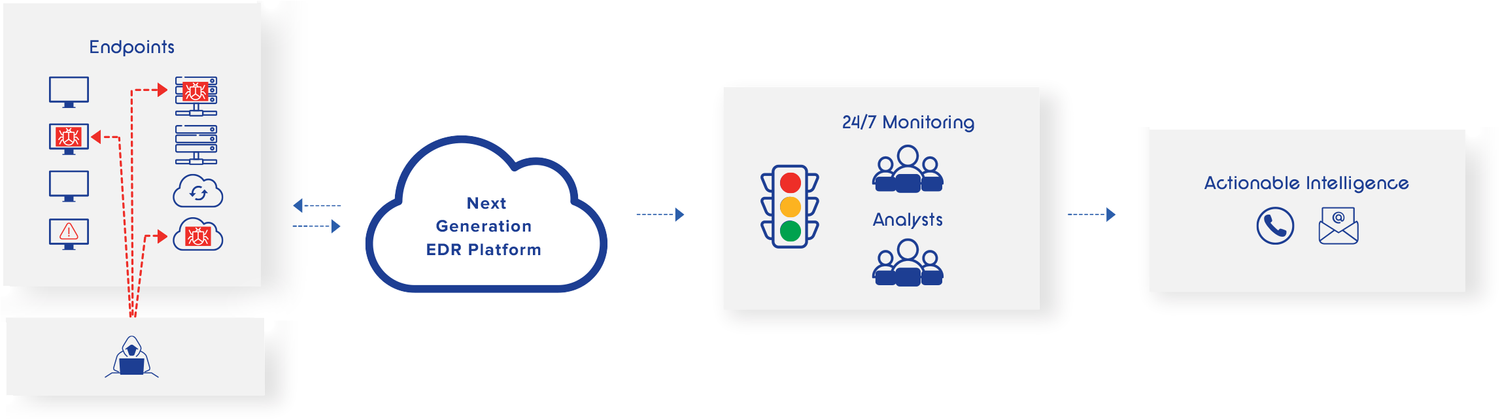 ZecureRight Protect empowers your organization with an array of invaluable benefits:
ZecureRight Protect empowers your organization with an array of invaluable benefits:
- Behavioral AI
- Easy Deployment and Maintenance
- Rapid Incident Response
- Enhanced Threat Visibility
- Rapid Rollback
- Protection Against Threats that Bypass Antivirus
Harnessing the power of Behavioral AI, ZecureRight Protect analyzes trillions of cyber threat data logs at the endpoint. It identifies malicious behavior, patterns of abnormal activity, and correlates these findings with real-time global threat hunting feeds, ensuring the most up-to-date detection.
ZecureRight Protect simplifies deployment with a guided onboarding service, making the process swift and uncomplicated. It also handles ongoing maintenance and updates for all existing and new endpoints within your network.
With powerful endpoint technology configured to perfection, the ZecureRight security team can swiftly respond and remediate on your behalf. This includes isolating infected systems, halting lateral movement, and preventing further compromise of your organization
ZecureRight Protect’s onboarding service streamlines deployment while efficiently managing the maintenance and updates for all your existing and new network endpoints, offering enhanced visibility into potential threats.
In the event of a successful endpoint exploitation, ZecureRight Protect provides an immediate and automated rollback to previous uncompromised versions. This feature saves you time and alleviates the challenges associated with traditional remediation methods that involve backup and disaster recovery systems.
ZecureRight Protect not only ensures an effortless deployment through guided onboarding but also manages ongoing maintenance and updates for all your existing and new network endpoints. Moreover, it provides protection against threats that manage to elude conventional antivirus measures.
User Awareness Training
When we look at where our biggest risk is from a cybersecurity perspective, the staff we rely on are still very much at the top of that list
Read MoreVulnerability Assessment
Our vulnerability assessment services help you assess on-premise hosts, databases, and web applications to identify potential configuration and asset management deficiencies
Read MoreWeb Penetration Testing
ZecureRight provides web application penetration testing for your business to improve its security. Web application penetration testing services proactively assess applications to identify vulnerabilities, such as those that could lead to unauthorized access,
Read MoreInfrastructure Penetration Testing
ZecureRight aims to defend businesses from cyber criminals. Infrastructure penetration testing is one of the main methods to use for securing your business and protecting your data.
Read MoreWireless Penetration Testing
Identify weaknesses, vulnerabilities and architectural flaws that would allow attackers to obtain sensitive information via a wireless solution.
Read MorePenetration Testing
ZecureRight offers a comprehensive suite of penetration testing services that deliver a tangible understanding of your organization’s IT security landscape.
Read More