
Through on-going education, we have the ability to turn this risk into our strongest line of defense. One that will also have a major impact on your organization’s overall security posture.
User awareness training is an educational process that helps increase employees’ understanding of data security policies, procedures, and best practices. It enables users to recognize common threats and attacks with the goal to reduce human error.
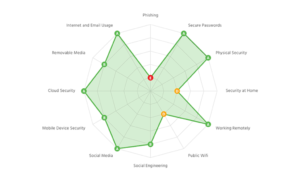
The main goal of user awareness training is to empower staff members with the knowledge needed to properly identify, handle, and protect any sensitive or private information they might encounter while using company computers or devices.
By having a comprehensive user awareness program in place, businesses are able to equip their employees with the tools needed to spot signs of phishing emails or other malicious content. In turn, this enables organizations to reduce their vulnerability against attacks from external sources.
The phishing simulation aspect of the service allows us to test the effectiveness of organizational policy and training by sending simulated phishing emails to employees and measuring their response. This helps to identify any areas where additional training may be needed and allows organizations to see the direct impact of their training efforts.
Additionally, such programs provide resources for IT departments (in case something goes wrong); users will be better equipped with information on how to respond when faced with cyber threats.
Identify weaknesses, vulnerabilities and architectural flaws that would allow attackers to obtain sensitive information via
Read MoreZecureRight offers a comprehensive suite of penetration testing services that deliver a tangible understanding of
Read MoreOne of the major challenges in cybersecurity is keeping up with the constantly evolving landscape
Read More